Read the article to know more about the power of Collective Knowledge of our Crowd of Ethical Hackers and how 2 of them received $46.000 as bounty for an Akamai misconfiguration.
Some Ethical Hackers of our Crowd earned $46.000 for finding an Akamai misconfiguration during a Bug Bounty Campaign in the UNGUESS platform. Let’s read this article to learn how they collaborated and shared their knowledge to reach that goal.
What is Collective Knowledge and how it works in Cybersecurity?
Collective knowledge is the capacity of groups of people to pool their experiences and knowledge and use that to solve problems and make smarter decisions.
Collective knowledge is widespread and plays an important role in modern life. It can be found in institutions such as the government, military, and universities, as well as social groups such as business and professional associations.
Collective intelligence can be measured by an organisation’s ability to achieve its goals by tapping into the collective knowledge of its members. This concept, as mentioned, can be applied in hundreds of situations or areas of work, including cybersecurity.
But, how?
In 2019, with 'The Biggest Weakness Is Our Biggest Strength: Cybersecurity in the Digital Age Is Crowdsourced', Gartner theorised how the ability to combine the complementary knowledge and expertise of cybersecurity experts in Crowd would be a powerful way to offer solutions and help organisations protect themselves from cybercrime.
Gradually, in addition to forums, blogs, online groups, specific government bodies, and non-profit associations, real companies have emerged that have made 'cybersecurity-made-in-the-crowd' a service and a product that can represent the collective intelligence with which corporate clients can enforce their Security Posture.
In concrete terms, imagine having access to a community of cyber experts, like Ethical Hackers, who can monitor every flaw, every vulnerability, and every point of exposure of your organisation to cyber risks.
How do these crowd-sourced services work?
3 are the fundamental elements:
- The Crowd, the community of certified Ethical Hackers
- A collaboration platform, to manage the community properly, in particular for governance and specific role responsibilities.
- Real-time reporting, to get insights as fast as possible and directly in the Information System to the right person
A client user can enter the platform, open a Bug Bounty (VAPT) campaign and call the Crowd to action to receive information on the real health status of their Security Posture, paying only per detected vulnerability.
By participating in these 'calls to action', researchers, Ethical Hackers in the Crowd, under the customer request, can help each other, collaborate, share information and support each other by sharing expertise.
This is the power of crowdsourcing in cybersecurity: harnessing talent, generating Collective Knowledge and producing better results for customers.
It is one of those cases where we could say that 1+1=3.
A concrete example? The Akamai misconfiguration worth $46,000 for 2 of our Ethical Hackers.
A few months ago, pushing the dynamics of the community, we decided to increase the collaboration within a group of Ethical Hackers. And that’s where Jacopo Tediosi and Francesco Mariani met each other.
Quite soon, working actively together, they understood and highlighted how manipulating a particular HTTP header made it possible to change the way reverse proxies communicated with each other and how this allowed them to perform different request smuggling attacks or, in particular cases, poison the server-side cache with arbitrary content on all Akamai Edge Nodes worldwide.
But how does this kind of cyber thread work?
As explained in the RFC 2068 — Section 13.5.1, there are some HTTP special headers named “hop-by-hop”, which are removed from proxies before forwarding requests to the next proxy or the destination.
The “Connection” header allows stating more “hop-by-hop” headers in addition to the default ones.
While testing on a UNGUESS internal Bug Bounty Program, specifying the “Connection-Length” header as “hop-by-hop”, it happened that Akamai’s first proxy removed it, turning the request body into a second request. Akamai’s second proxy then resolved the two requests separately.
As explained in the following flowchart, since the first proxy received two responses but only one was expected, a desynchronization occurred, and the second response was queued and subsequently sent in response to requests from other clients/users, causing an HTTP Smuggling Vulnerability.
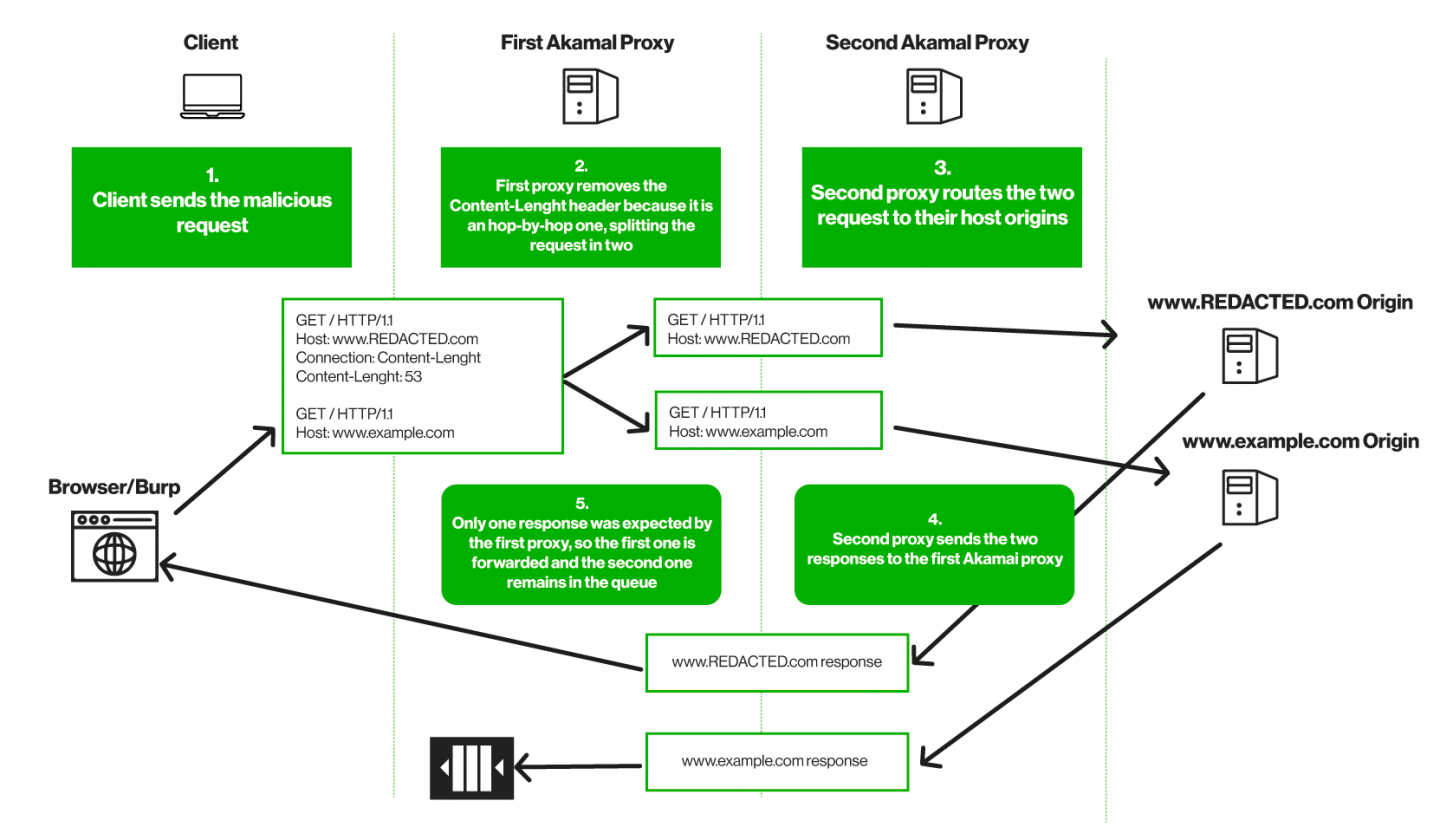
The payload was built step-by-step by both our testers, who studied and smartly mixed its pieces until it worked. Both agreed that each other's skills were crucial in arriving at the final result.
Later, they discovered the vulnerability affected any website served by Akamai's network, and, with UNGUESS' active support, they initiated a coordinated process of responsible disclosure to Akamai and its major customers.
Please refer to Jacopo and Francesco’s blog posts for more tech information.
Do you want to join our community of Ethical Hackers? Subscribe here: JOIN THE COMMUNITY