A Bug Bounty Program is an initiative launched by a company to engage ethical hackers in the search for bugs , vulnerabilities and exploits. The main advantage it offers is to extend problem research to a diverse mass of professionals, stimulated by rewards that lead them to always give their best.
However, by its nature, a Bug Bounty Program requires expertise and dedication to be best organized, so much so that smaller companies often prefer to rely on more traditional methods for security. In this article, we show how, with the help of a trusted partner, a Bug Bounty Program can prove to be an effective and efficient tool for any business entity.
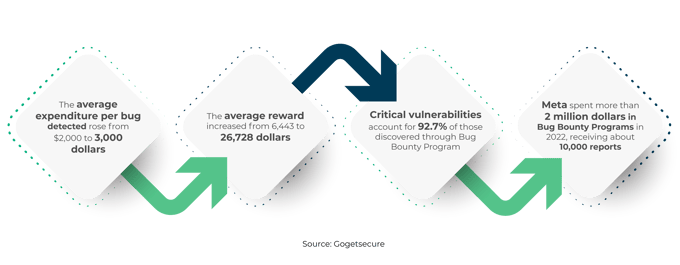
Fonte: Gogetsecure
The Critical Issues of a Bug Bounty Program
At UNGUESS, from the very beginning, we posed the problem of how any company could develop a quality Bug Bounty Program that could attract some of the best ethical hackers, despite not having facilities and availability comparable to those of giants like Google, Meta or Microsoft. To do so, we started by considering the critical issues of a Bug Bounty Program.
A critical mission
Contrary to what the collective imagination shows, a Bug Bounty Program is not a generic call to arms via a post on the company website or social media. On the contrary, it is a very complex activity both in terms of initiation and management. And if this is true for companies already well-versed in the world of cybersecurity, let alone those that are somewhat unfamiliar with the subject. Because organizing a Bug Bounty Program requires knowing the precepts of corporate IT security, but also the ethical and technical basics involved in bug hunting.
The boomerang risk
Not to mention that you have to know where to look and how to choose the best ethical hacks, how to set up the reward plan, and much more. An immense amount of work, requiring time and resources and which, if not done properly, can result in a resounding boomerang. Perhaps because you are not getting the results you hoped for, or because the mad and desperate hunt for professionals leads to sharing sensitive information with unknown actors. And even if the startup phases of the Bug Bounty Program are organized as well as possible, there is a risk that the execution will turn into a half disaster.
A Bug Bounty Program needs excellent organization
An eagerness to organize a Bug Bounty Program in a big way may lead to a large mass of ethical hackers moving unchecked through the corporate network. It happens when the Bug Bounty Program lacks coordination and continuous management of the resources in play. In this case, the result can lead to numerous problems.
For example, network saturation, when multiple exploiting attempts are not found due to unclear regulations or poor profiling of the professionals involved in the project. When this happens, internal security teams, which are responsible for managing the network, are inundated with reports that are difficult to filter and verify with the right timing.
If trust is lacking
The results can be catastrophic, since among the activities pertaining to a Bug Bounty Program there may be hidden some that are actually malicious, carried out by real cybercriminals, who could take advantage of the confusion of the moment in the face of inadequate monitoring systems.
This is how you run into the real risk of Bug Bounty Programs: with a lack of proper monitoring, they can turn into dramatic experiences that, instead of leading to tangible results, can become a source of major efficiency and business continuity problems for the company.
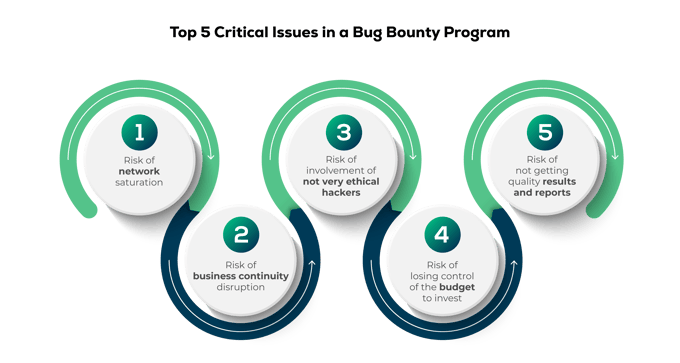
Then there is the issue of trust. A loosely managed Bug Bounty Program can result in thousands of ethical hackers at work on the network, among whom some may be hiding with ill-defined intentions. A middle ground between a grey hat hacker and a black hat hacker, or simply an individual who poses as an ethical hacker but then outsources their work to other actors on a contract basis.
The company, at this point, loses control of the program, and the Bug Bounty Program experience proves so bad that it discourages an activity that is now indispensable.
 Fonte: Gogetsecure.
Fonte: Gogetsecure.
A platform to help your Bug Hunting Program
At UNGUESS we have found a solution to all these, and other, critical issues by creating UNGUESS SECURITY, a crowdsourced ethical hacking platform under our coordination. A real community of professionals who are selected by our team, based on very strict requirements both in terms of technical competence and integrity.
With our platform, the ethical hacker stops being an obscure individual to whom we entrust a company’s network while keeping our fingers crossed, and instead becomes a trusted resource, known and ready to put himself at the service of a company’s security.
A community of ethical hackers
In this environment, where participants go through a strict selection, we built a reliable community of more than 500 ethical hackers, trusted by companies of all sizes, from small businesses to multinational corporations.
Those who choose our platform no longer have to worry about the management of the Bug Bounty Program, but only need to give the necessary guidance to achieve the designated security goals. Everything else is handled by the platform at every stage of the program:
- organization,
- startup,
- management,
- closing,
- reporting.
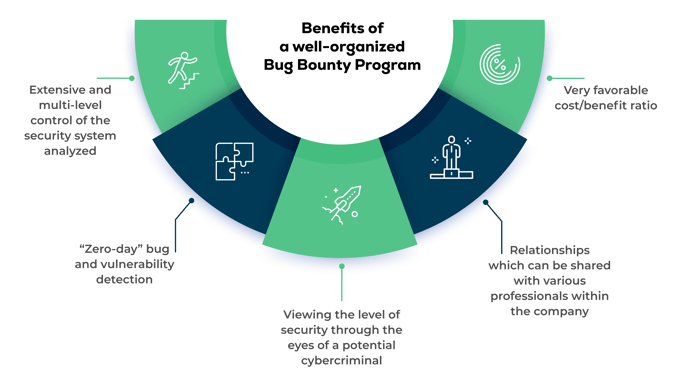
The full benefits of our Bug Hunting Program
The UNGUESS SECURITY platform is a useful tool not only for companies, but also for ethical hackers themselves, who choose us to avoid bureaucratic and organizational hassles and be able to focus on the actual analysis. A concept that appeals to the best ethical hackers and propels the success of our platform.
The UNGUESS SECURITY platform also represents a valuable point of contact between two worlds, ethical hacking and business, which until now struggled to interact because they lacked a figure to act as a guarantor for both parties. Today that figure exists, and it’s called UNGUESS SECURITY.